本文最后更新于 694 天前,其中的信息可能已经过时,如有错误请发送邮件到wuxianglongblog@163.com
K8S集群的附加组件相关配置实战案例
一.coredns附加组件初体验
1.新版本中的DNS组件变更为coredns
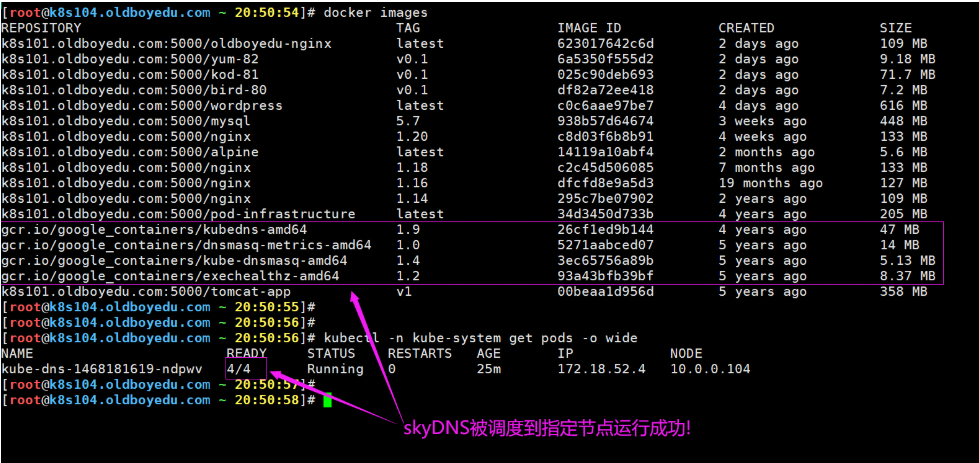
在早期K8S版本中,我们需要手动部署skydns附加组件,而且该组件需要一个Pod内需要4个容器哟。
如下图所示,在新版本中,并不需要咱们手动部署skydns啦,取而代之的则是coredns附加组件哟~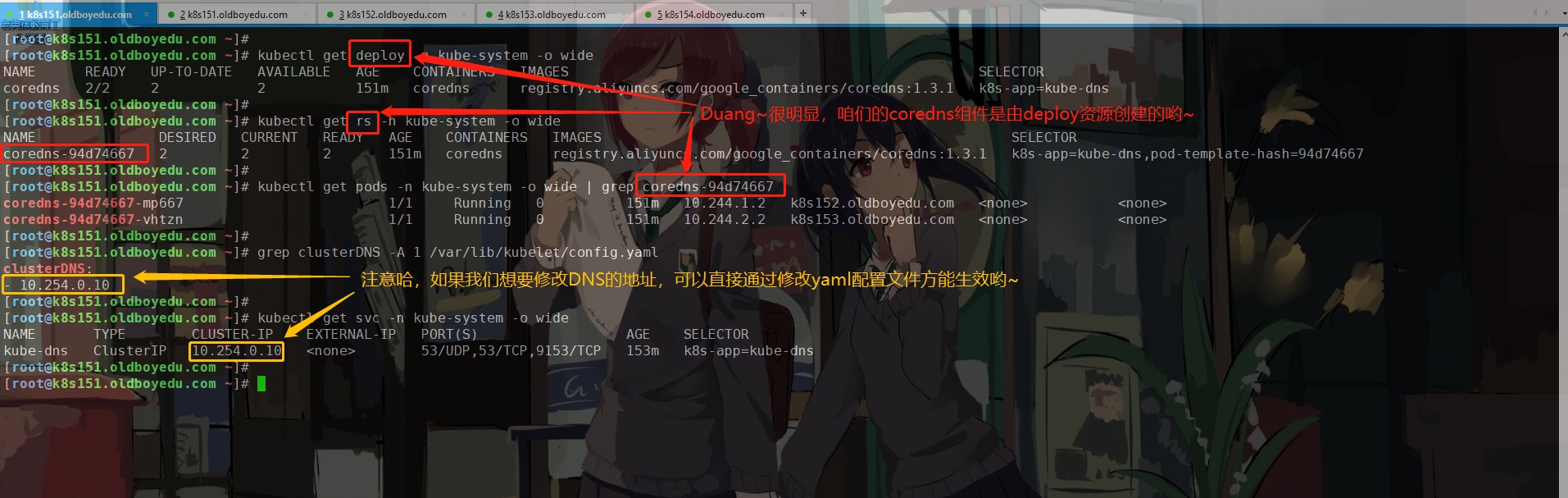
2.验证coreDNS的可用性
(1)安装测试工具
yum -y install bind-utils
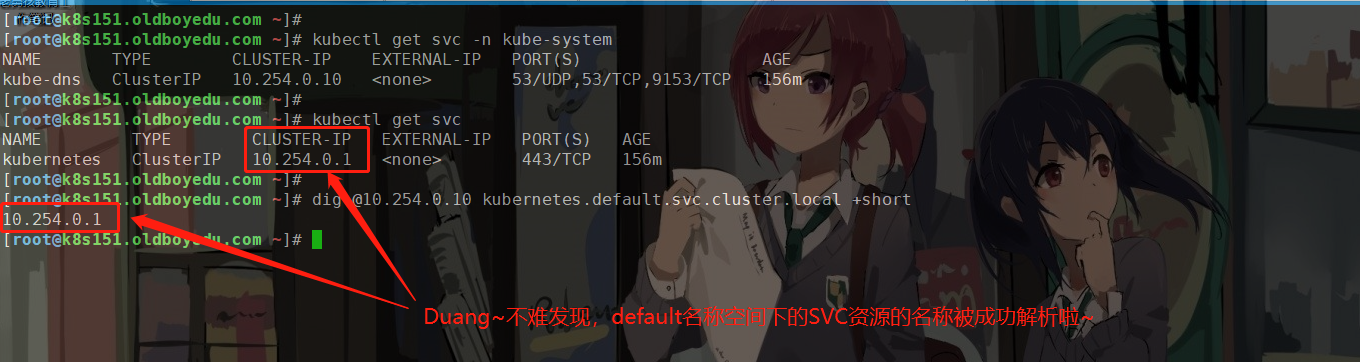
(2)测试default名称空间下的svc资源是否可以正常解析
dig @10.254.0.10 kubernetes.default.svc.cluster.local +short
3.课堂练习
(1)修改api-server配置参数,将svc的绑定node节点pod范围进行更改
vim /etc/kubernetes/manifests/kube-apiserver.yaml
...
spec:
containers:
- command:
- kube-apiserver
- --service-node-port-range=3000-50000 # 我只添加了这一行哟~
...
(2)课堂练习
1)为了进一步测试coreDNS,请将之前讲解的tomcat-demo案例进行测试!
2)要求tomcat访问8080端口就可以访问到服务哟~
推荐阅读:
https://kubernetes.io/zh/docs/concepts/services-networking/service/#nodeport
温馨提示:
由于apiserver组件是一个静态Pod,因此无需重启服务,当我们修改配置文件后,其会自动更新Pod哟~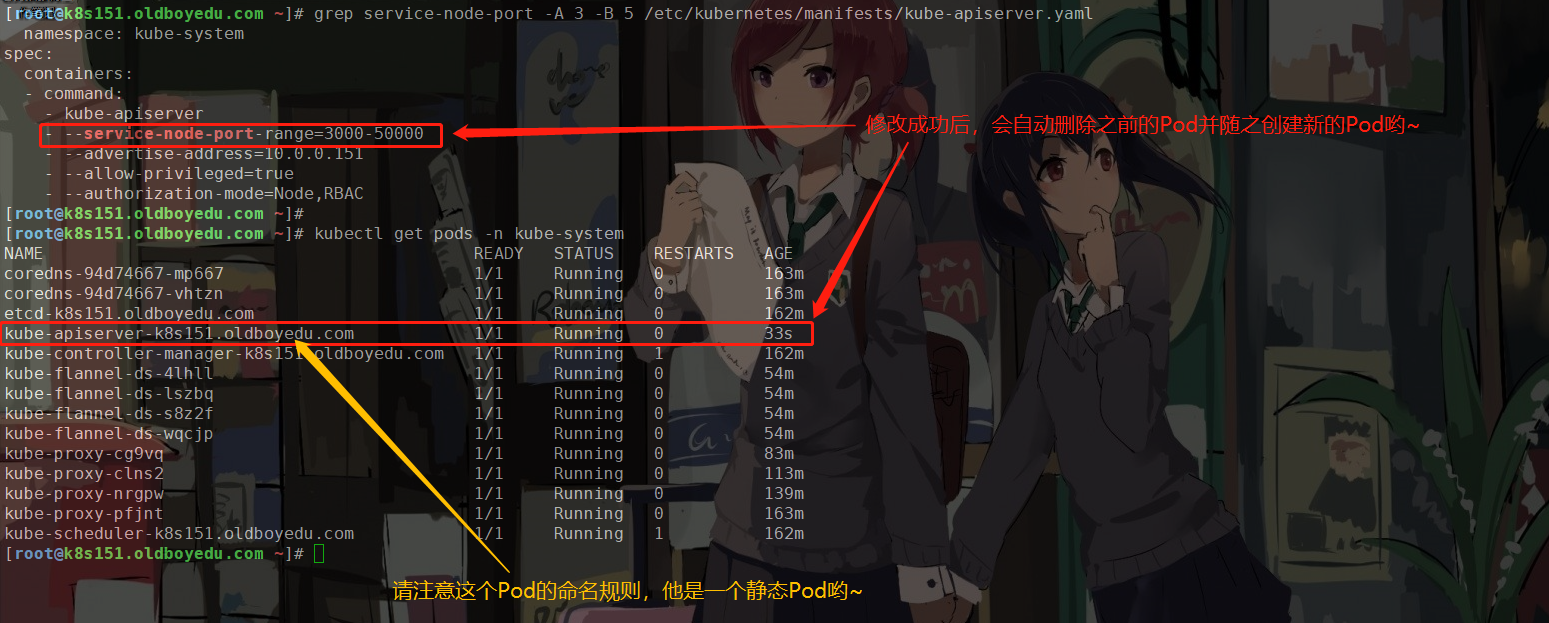
二.部署dashboard组件
1.dashboard概述
关于dashboard的介绍我这里就不罗嗦啦,上一次相信大家多少对咱们的集群有一定的了解。
推荐阅读:
https://kubernetes.io/docs/concepts/cluster-administration/addons/
https://github.com/kubernetes/dashboard#install2.部署dashboard组件
(1)下载部署dashaboard的资源清单
curl -o kubenetes-dashboard.yaml https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
(2)下载镜像
docker pull registry.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1
docker image tag registry.aliyuncs.com/google_containers/kubernetes-dashboard-amd64:v1.10.1 k8s101.oldboyedu.com:5000/kubernetes-dashboard-amd64:v1.10.1
docker image push k8s101.oldboyedu.com:5000/kubernetes-dashboard-amd64:v1.10.1
(3)修改镜像地址(指定咱们上传的dashboard镜像即可)
vim kubenetes-dashboard.yaml
...
image: k8s101.oldboyedu.com:5000/kubernetes-dashboard-amd64:v1.10.1
(4)修改SVC信息(仅需修改如下所示2点即可)
tail -15 kubenetes-dashboard.yaml
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort # 此处是我添加的
ports:
- port: 443
targetPort: 8443 # 此处也是我添加的哈!
nodePort: 38443
selector:
k8s-app: kubernetes-dashboard
(5)应用配置文件
kubectl apply -f kubenetes-dashboard.yaml
3.使用默认的token登录,权限不足
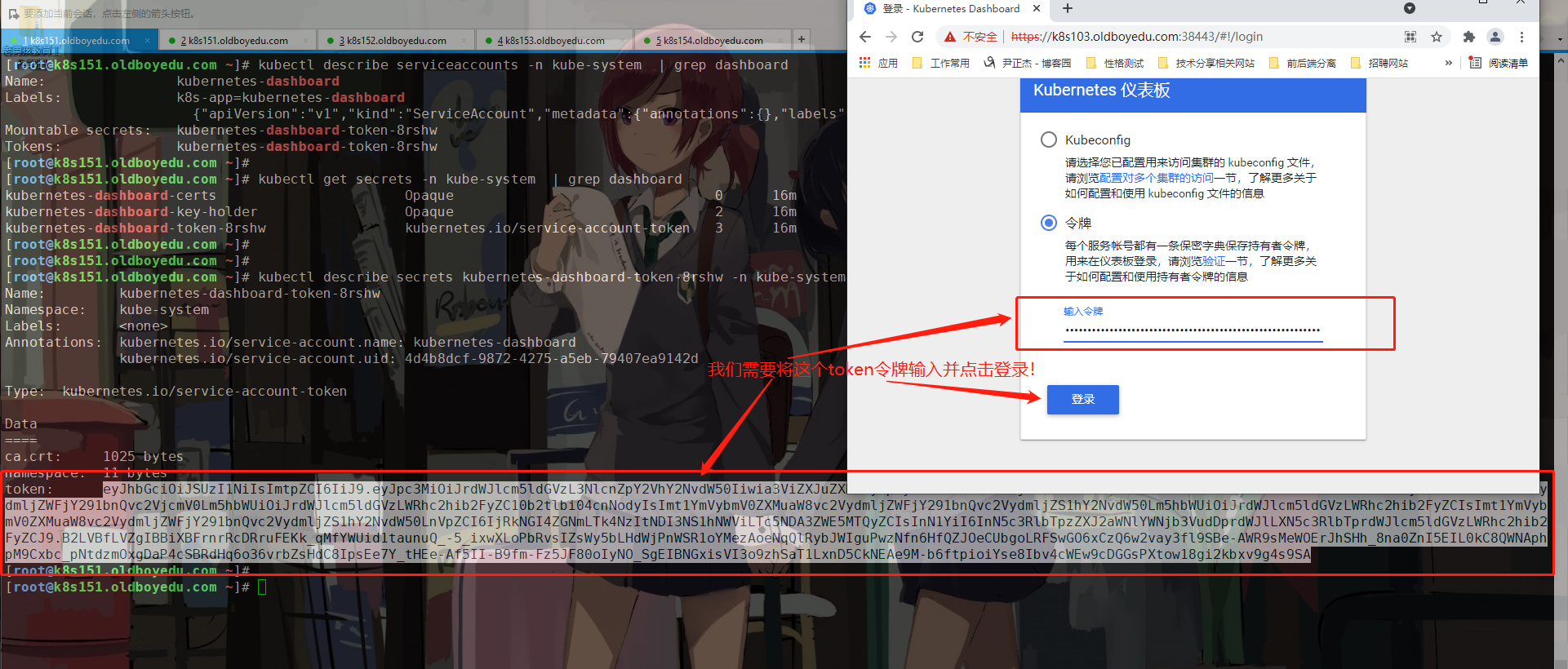
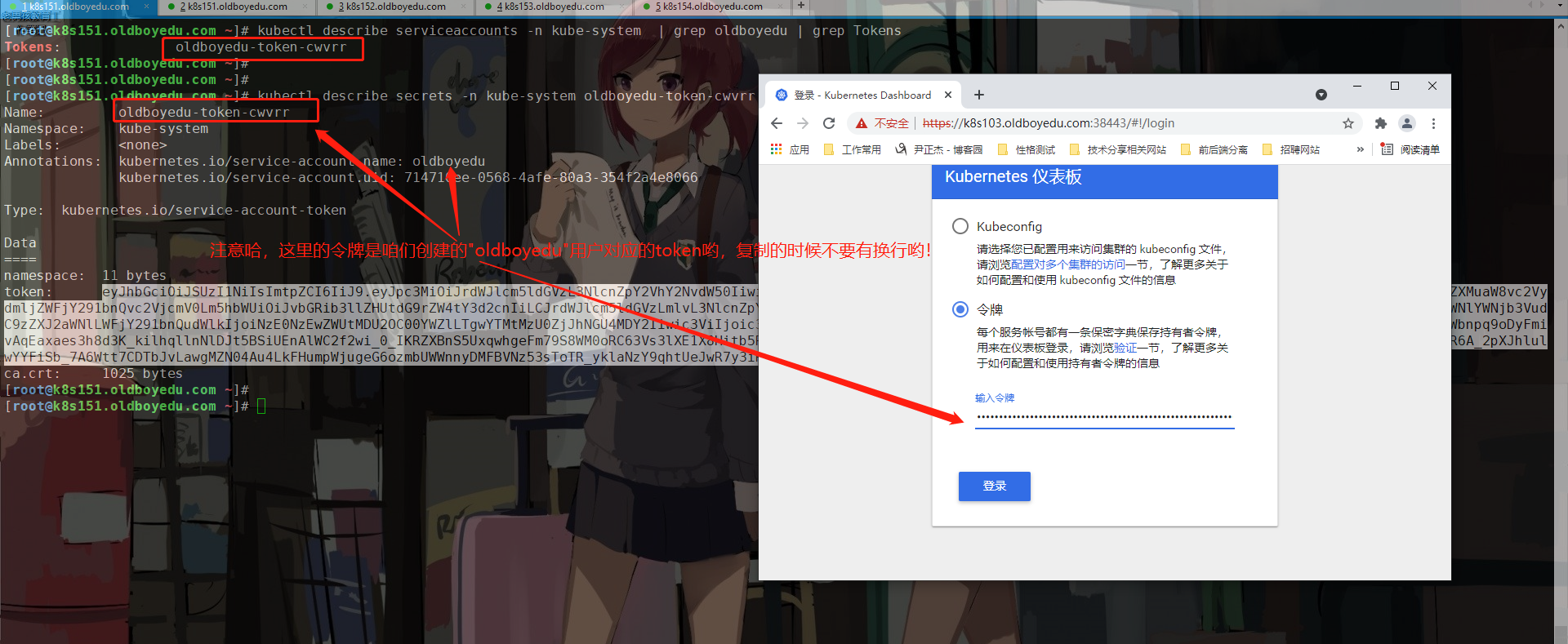
(1)查看sa资源的Tokens信息
kubectl describe serviceaccounts -n kube-system | grep kubernetes-dashboard | grep Tokens
(2)如上图所示,根据上一步就能的出来"kubernetes-dashboard-token-8rshw"存储着Tokens信息哟
kubectl describe secrets kubernetes-dashboard-token-8rshw -n kube-system
温馨提示:
如下图所示,如果咱们使用sa资源的token信息发现始终无法正常登录集群哟~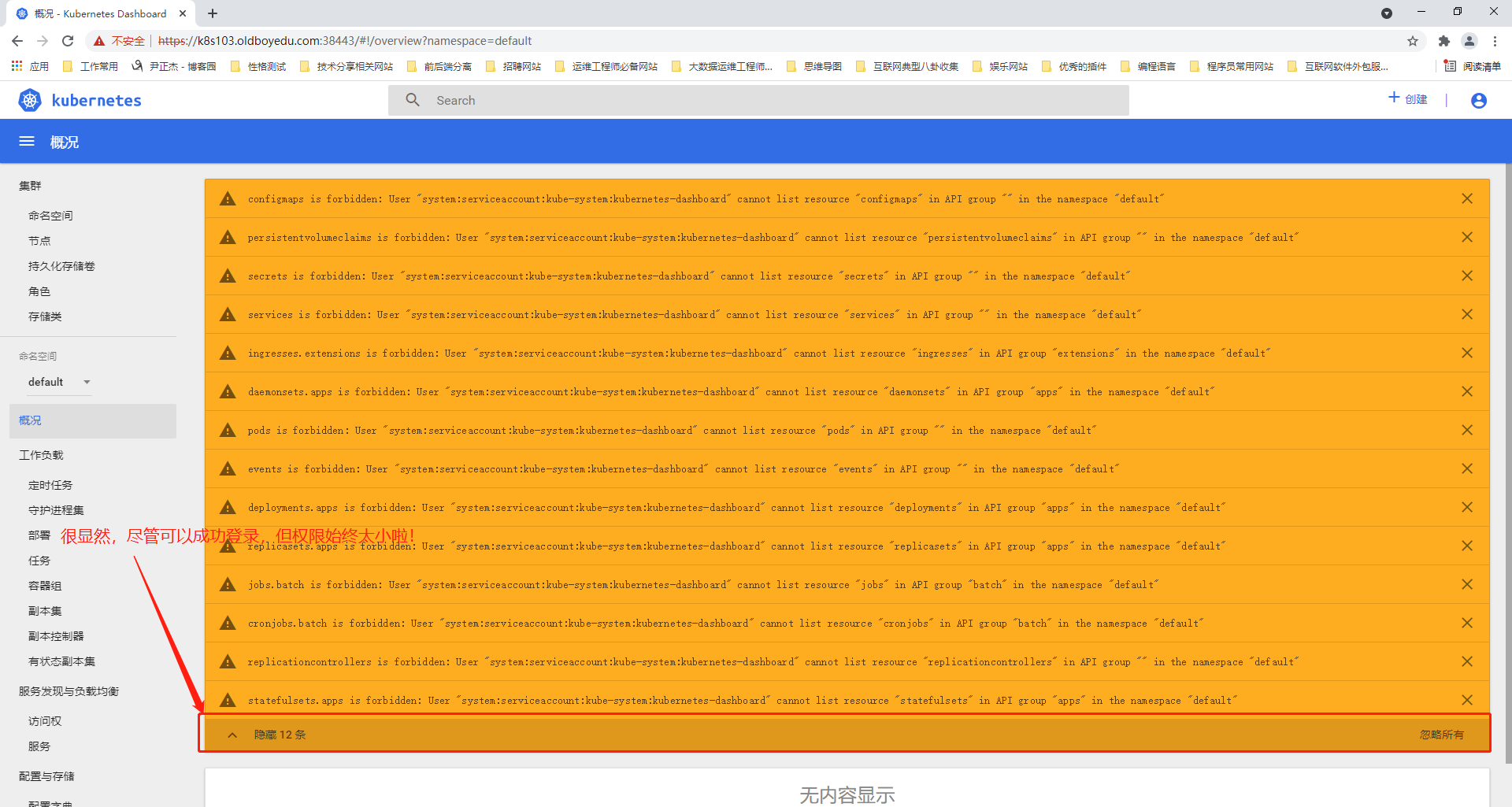
4.自定义用户登录
(1)编写K8S的yaml资源清单文件
[root@k8s101.oldboyedu.com ~]# cat oldboyedu-dashboard-rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
# 创建一个名为"oldboyedu"的账户
name: oldboyedu
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
# 既然绑定的是集群角色,那么类型也应该为"ClusterRole",而不是"Role"哟~
kind: ClusterRole
# 关于集群角色可以使用"kubectl get clusterrole | grep admin"进行过滤哟~
name: cluster-admin
subjects:
- kind: ServiceAccount
# 此处要注意哈,绑定的要和我们上面的服务账户一致哟~
name: oldboyedu
namespace: kube-system
[root@k8s101.oldboyedu.com ~]#
(2)创建资源清单
[root@k8s101.oldboyedu.com ~]# kubectl apply -f oldboyedu-dashboard-rbac.yaml
serviceaccount/oldboyedu created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
[root@k8s101.oldboyedu.com ~]#
(3)查看sa资源的Tokens信息
kubectl describe serviceaccounts -n kube-system oldboyedu | grep Tokens
kubectl -n kube-system describe secrets oldboyedu-token-6ntzp # 根据上一步的token名称
温馨提示:
如下图所示,由于咱们创建的ServiceAccount绑定的角色为"cluster-admin"这个角色,因此oldboyedu用户的token是可以访问集群的所有资源的哟~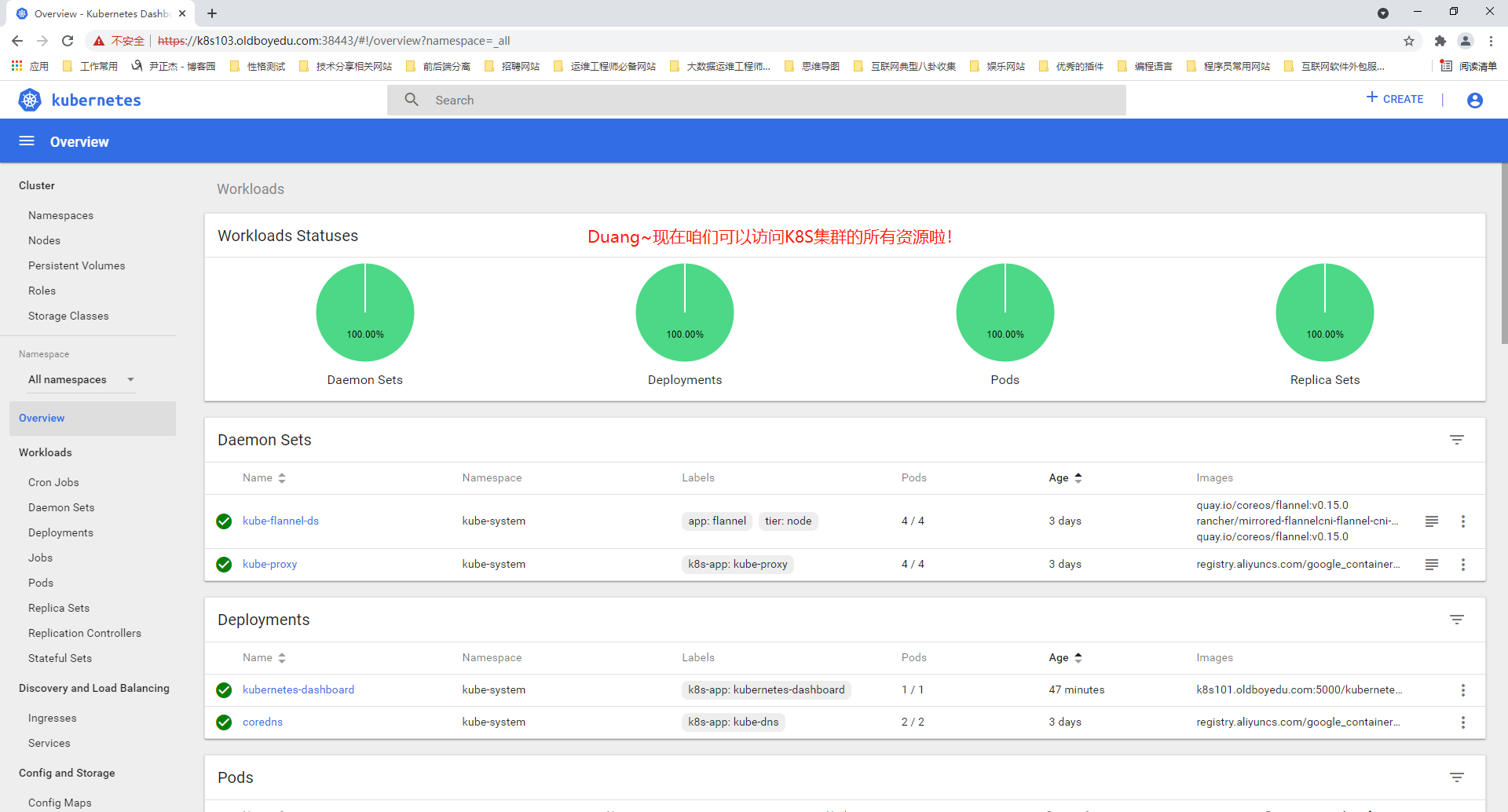
5.基于kubeconfig文件访问K8S集群
(1)编写生成kubeconf的配置文件的脚本
cat > oldboyedu-generate-context-conf.sh <<'EOF'
#!/bin/bash
# auther: Jason Yin
# 获取secret的名称
SECRET_NAME=`kubectl get secrets -n kube-system | grep oldboyedu | awk {'print $1'}`
# 指定API SERVER的地址
API_SERVER=k8s201.oldboyedu.com:6443
# 指定kubeconfig配置文件的路径名称
KUBECONFIG_NAME=/root/oldboyedu-k8s-dashboard-admin.conf
# 获取oldboyedu用户的tocken
OLDBOYEDU_TOCKEN=`kubectl get secrets -n kube-system $SECRET_NAME -o jsonpath={.data.token} | base64 -d`
# 在kubeconfig配置文件中设置群集项
kubectl config set-cluster oldboyedu-k8s-dashboard-cluster --server=$API_SERVER --kubeconfig=$KUBECONFIG_NAME
# 在kubeconfig中设置用户项
kubectl config set-credentials oldboyedu-k8s-dashboard-user --token=$OLDBOYEDU_TOCKEN --kubeconfig=$KUBECONFIG_NAME
# 配置上下文,即绑定用户和集群的上下文关系,可以将多个集群和用户进行绑定哟~
kubectl config set-context oldboyedu-admin --cluster=oldboyedu-k8s-dashboard-cluster --user=oldboyedu-k8s-dashboard-user --kubeconfig=$KUBECONFIG_NAME
# 配置当前使用的上下文
kubectl config use-context oldboyedu-admin --kubeconfig=$KUBECONFIG_NAME
EOF
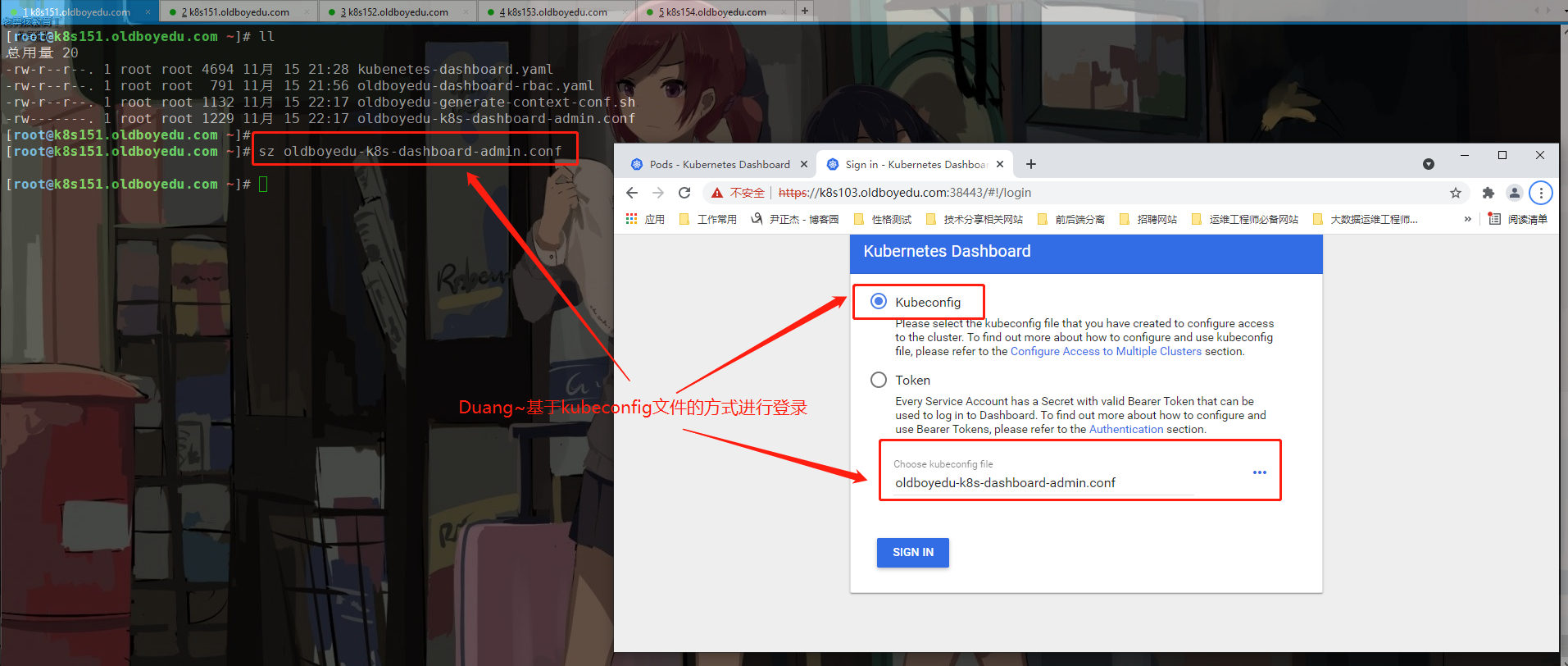
(2)运行上述脚本并下载上一步生成的配置文件到桌面,如上图所示,选择并选择该文件进行登录
sz oldboyedu-k8s-dashboard-admin.conf
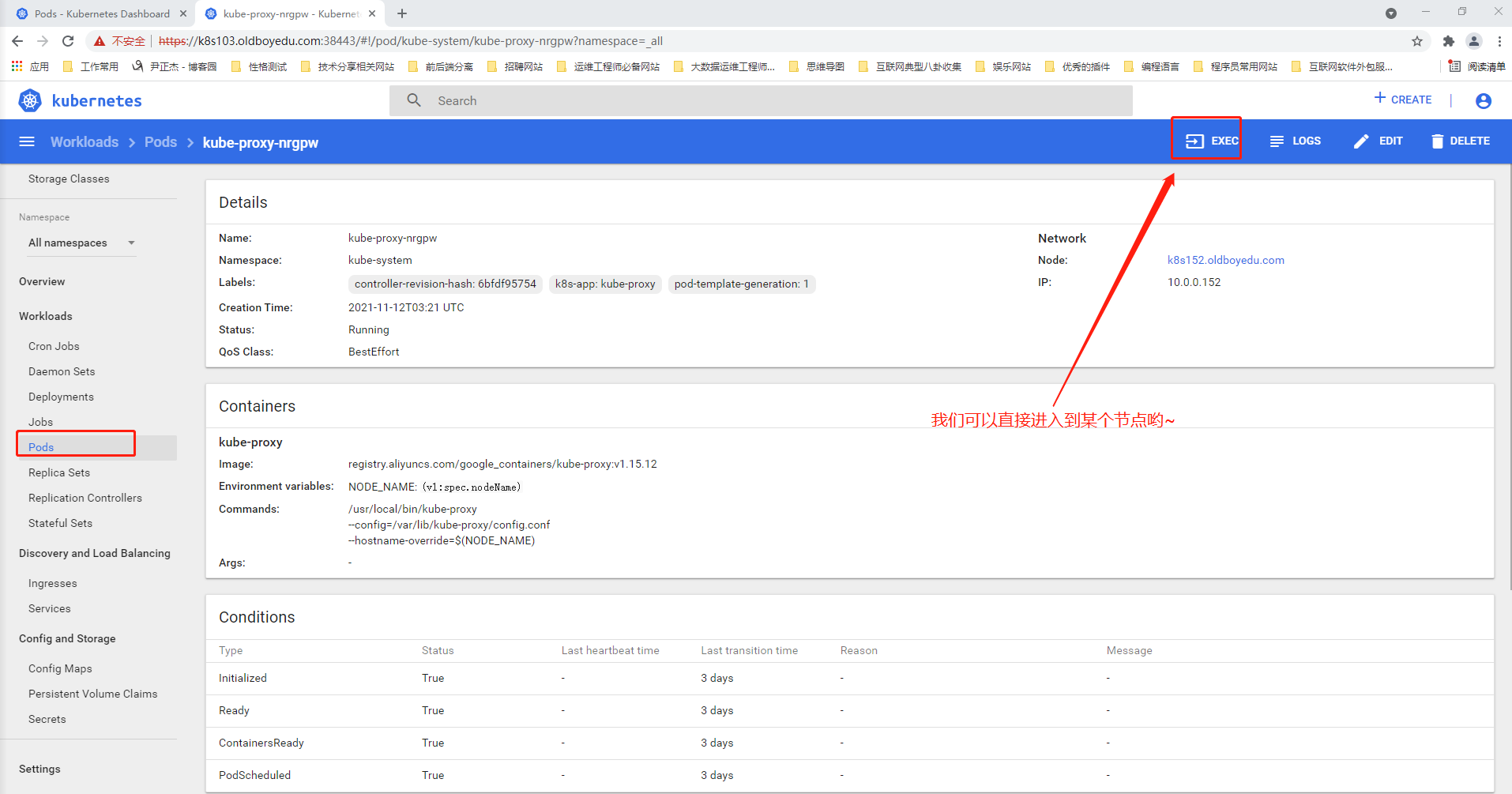
(3)进入到dashboard的WebUI
如下图所示,我们可以访问任意的Pod,当然也可以直接进入到有终端的容器哟
三.基于metrics组件实现水平弹性伸缩实战案例
1.测试环境
温馨提示:
实现的前提请保证metrics附加组件是成功部署的!
cat > 01-deploy-mysql.yaml <<'EOF'
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: oldboyedu-mysql
namespace: oldboyedu-tomcat
spec:
replicas: 1
template:
metadata:
labels:
app: oldboyedu-tomcat-mysql
spec:
containers:
- name: mysql
image: k8s201.oldboyedu.com:5000/mysql:5.7
ports:
- containerPort: 3306
env:
- name: MYSQL_ROOT_PASSWORD
value: "123456"
EOF
cat > 02-deploy-mysql-svc.yaml <<'EOF'
kind: Service
apiVersion: v1
metadata:
name: oldboyedu-mysql-svc
namespace: oldboyedu-tomcat
spec:
type: ClusterIP
clusterIP: 10.254.100.136
ports:
- port: 3306
protocol: TCP
targetPort: 3306
selector:
app: oldboyedu-tomcat-mysql
EOF
cat > 03-deploy-tomcat.yaml <<'EOF'
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: oldboyedu-tomcat
namespace: oldboyedu-tomcat
spec:
replicas: 1
template:
metadata:
labels:
app: oldboyedu-tomcat-app
spec:
containers:
- name: myweb
image: k8s201.oldboyedu.com:5000/tomcat-app:v1
ports:
- containerPort: 8080
env:
- name: MYSQL_SERVICE_HOST
value: oldboyedu-mysql-svc
- name: MYSQL_SERVICE_PORT
value: '3306'
resources:
requests:
cpu: 100m
limits:
cpu: 100m
EOF
cat > 04-deploy-tomcat-svc.yaml <<'EOF'
kind: Service
apiVersion: v1
metadata:
name: oldboyedu-tomcat-svc
namespace: oldboyedu-tomcat
spec:
type: NodePort
ports:
- port: 8080
protocol: TCP
targetPort: 8080
nodePort: 8080
selector:
app: oldboyedu-tomcat-app
EOF
cat >05-ns-oldboyedu-tomcat.yaml <<'EOF'
kind: Namespace
apiVersion: v1
metadata:
name: oldboyedu-tomcat
EOF2.创建hpa规则
kubectl -n oldboyedu-tomcat autoscale deployment.apps/oldboyedu-tomcat --min=2 --max=5 --cpu-percent=103.压测
ab -c 1000 -n 2000000 http://10.0.0.203:8080/demo四.可能会出现的报错
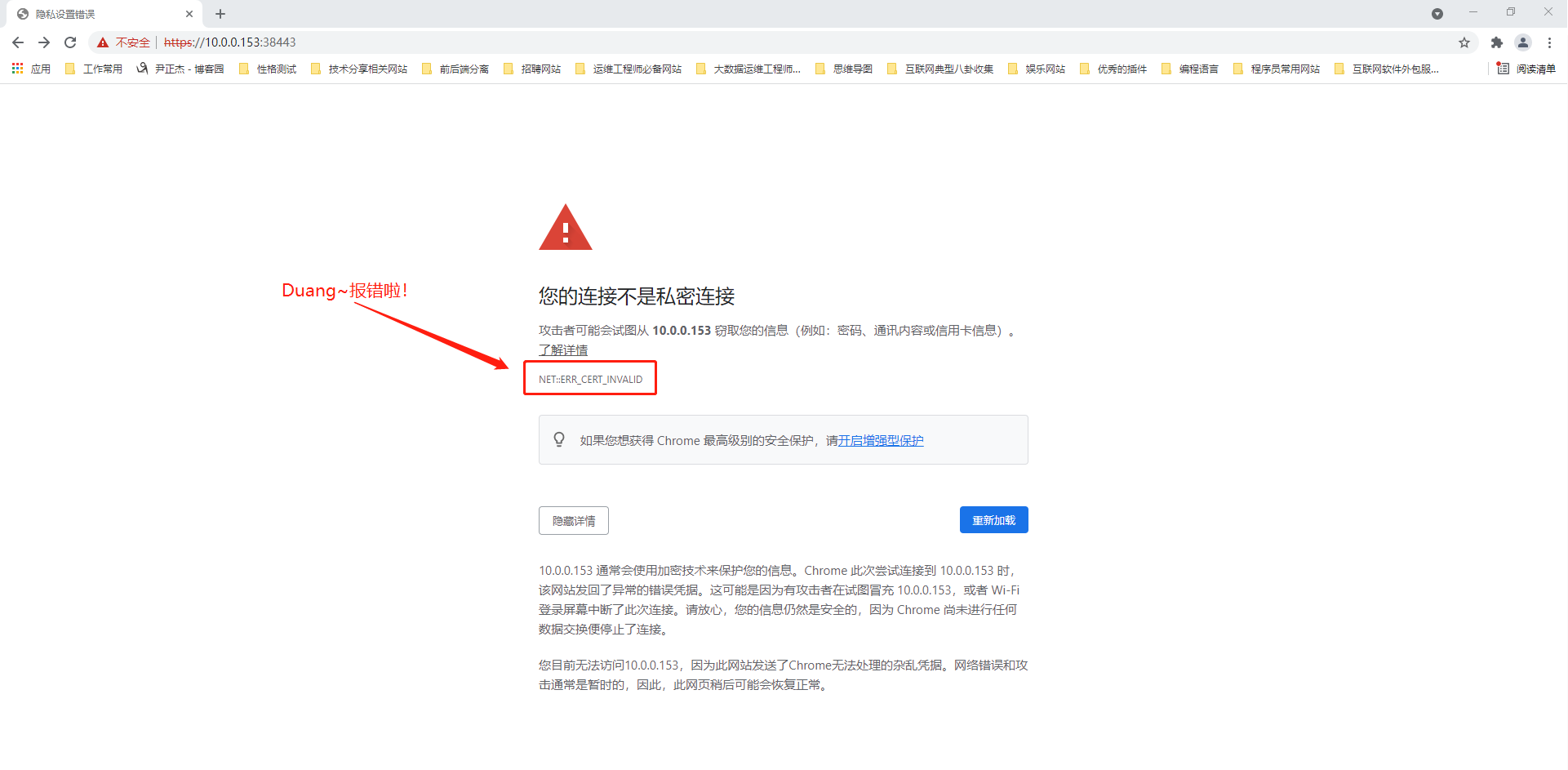
1.chrome提示NET::ERR_CERT_INVALID
错误原因:
证书无效。
解决方案:
方法一:
添加自用的CA证书到 证书管理器里
方法二:
在Chrome提示“您的连接不是私密连接”页面的空白区域点击一下,然后输入“thisisunsafe”(页面不会有任何输入提示),输入完成后会自动继续访问